XDR * eBPF = CADR
After writing the eBPF for the Infrastructure Platform whitepaper for the eBPF foundation, I find myself referencing one of my older posts:
With EDR:
➡️You install a user-space agent on an end-user device or on a server
➡️Collect some logs
➡️Break every IT system in July 2024
➡️Complain that you can’t secure cloud workloads
➡️Dedicate 20% of your CPU to the EDR sensor
sO wHy NoT bRiNg THiS tO My ClOUd
Enter XDR
.
.
.
Exit XDR
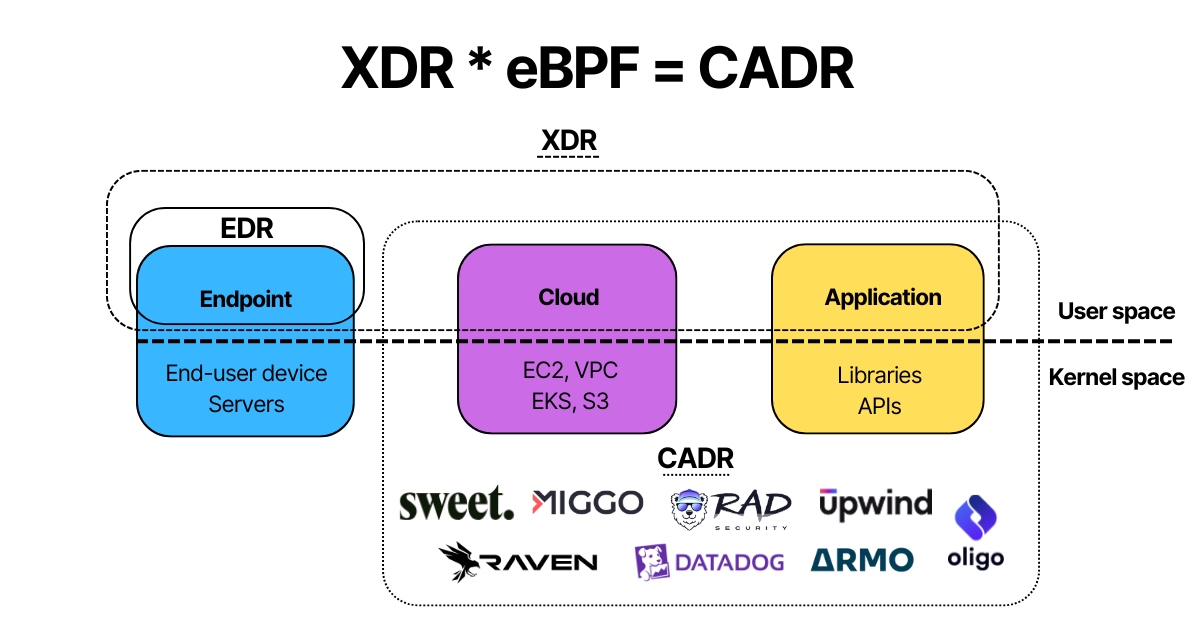
XDR is a low quality initiative to extend EDR beyond the endpoint. But using the same user-space agents that traditional AV and EDR solutins are, XDR can’t do much more. As such, these guys can use eBPF for lightweight and better controls over the kernel. This can bring the endpoint benefits of EDR to network, process, application, containers, APIs, and the like. This XDR with eBPF combo sounds a lot like James Berthoty‘s Cloud App Detection and Response (CADR).
Not only do you have kernel-level controls, but user-space agents have a high performance tax. eBPF dramatically reduces observability overhead by collecting metrics, logs, and traces directly in kernel space without expensive system calls. It can implement efficient memory management policies, custom garbage collection triggers, and event monitoring strategies that minimize operational overhead. Some eBPF-based agents and sensors can introduce as little as a 2% CPU load increase relative to baseline levels, and near-zero memory increase.
Looking at his Runtime Cloud Security in 2025, the most complete CADR solutions are heavily based on eBPF. The likes of:
Spyderbat
Oligo Security
ARMO
RAD Security
Datadog
Raven.io
Sweet Security
Upwind Security
Miggo Security
Skyhawk Security
While eBPF is not the only technology that define what CADR is or what it can be, the kernel-level control and visibility is definitely a missing piece on what XDR vendors have been trying to do wholly in the user space.
As the comments on my previous post noted, eBPF has great benefits, but like every other cybersecurity technology, it bounds to its own limits - and in the runtime detection case, the syscalls it monitors.


Great summary but what about windows?
https://gen0sec.com Synapse is also an alternative - https://github.com/gen0sec/synapse.